Scammers find sneaky way to bypass your iPhone’s safety features
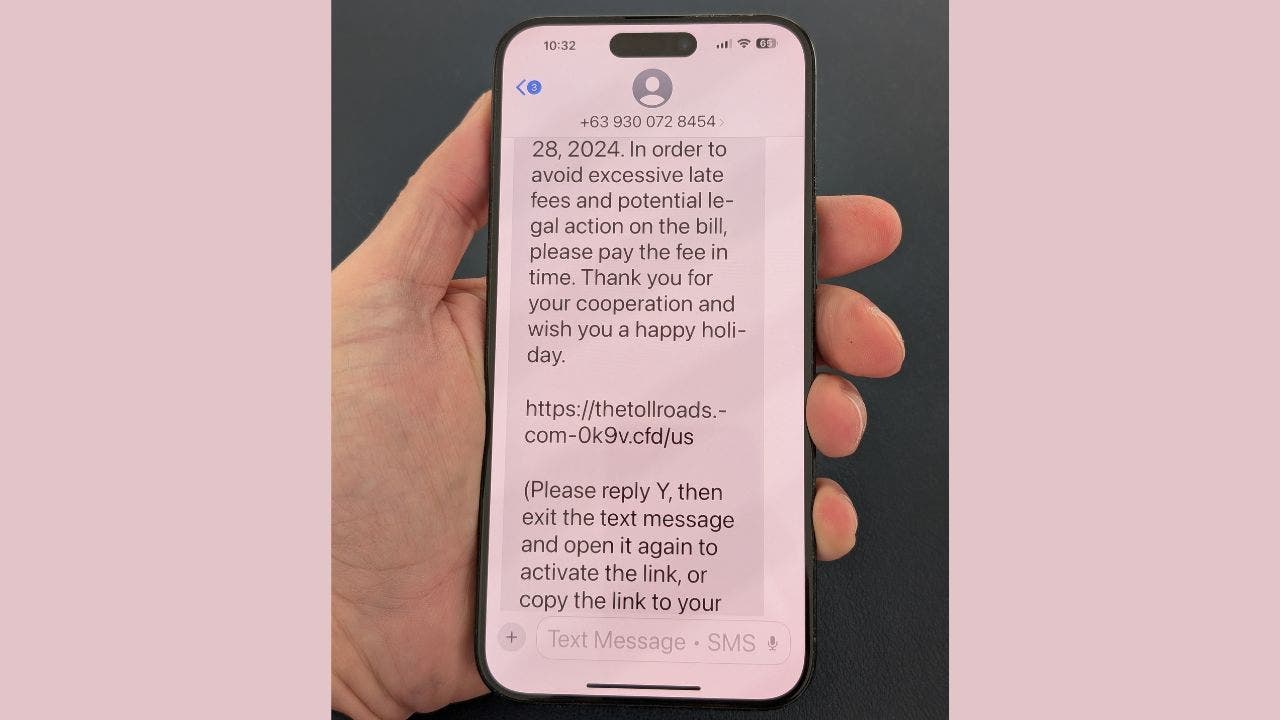
The ever-evolving landscape of cybercrime has taken a new turn as cybercriminals have found a way to bypass Apple’s built-in phishing protection for iMessage. This alarming development exposes users to malicious links and potential scams, turning a security feature into a vulnerability that could have significant personal and financial consequences.
The sophisticated tactic involves exploiting Apple’s automatic disabling of links in messages from unknown senders. By instructing recipients to reply to the message, often with a simple “Y,” cybercriminals can re-enable these disabled links. This seemingly harmless action not only activates the links but also signals to scammers that they have found an engaged target for future attacks.
This new method is just one part of a broader trend of smishing (SMS phishing) attacks targeting mobile users. As smartphones become increasingly integral to our daily activities, including financial transactions and personal communications, these attacks pose a significant threat to users’ security and privacy.
To protect yourself from falling victim to these sophisticated phishing attempts, consider the following steps:
1. Never reply to suspicious messages: Avoid responding to texts from unknown senders, especially those asking you to reply to activate links. Delete suspicious messages and block the sender to prevent further attempts.
2. Verify sender identity: Contact organizations directly through official channels if you are unsure about a message’s legitimacy.
3. Be skeptical of urgency: Scammers often use urgent language to prompt quick, thoughtless actions.
4. Enable message filtering: Use your device’s built-in filtering options to sort messages from unknown senders automatically.
5. Use two-factor authentication (2FA): Add an extra layer of security to your accounts by requiring a second form of verification in addition to your password.
6. Install strong antivirus software: Protect yourself from malicious links that install malware by having antivirus software installed on all your devices.
7. Consider personal data removal services: By reducing your online footprint, you make it harder for cybercriminals to obtain your contact information and target you with deceptive messages.
If you suspect you have been targeted in a smishing attack, report the incident to relevant authorities and institutions, freeze your credit, change passwords for all your accounts, monitor your finances for suspicious activity, and consider using an identity theft protection service.
By remaining cautious and following best practices for digital security, you can significantly reduce your risk of falling victim to these sophisticated phishing attempts. Stay informed, stay vigilant, and protect yourself from cyber threats in an ever-changing digital landscape.




